HISTORY OF CYBER SECURITY AND CYBER SECURITY GOALS
History of Cyber Security
The origin of cybersecurity began with a research project. It only came into existence because of the development of viruses.
How did we get here?

In 1969, Leonard Kleinrock, professor of UCLA and student, Charley Kline, sent the first electronic message from the UCLA SDS Sigma 7 Host computer to Bill Duvall, a programmer, at the Stanford Research Institute. This is a well-known story and a moment in the history of a digital world. The sent message from the UCLA was the word "login." The system crashed after they typed the first two letters "lo." Since then, this story has been a belief that the programmers typed the beginning message "lo and behold." While factually believed that "login" was the intended message. Those two letters of messages were changed the way we communicate with one another.

In 1970's, Robert (Bob) Thomas who was a researcher for BBN Technologies in Cambridge, Massachusetts created the first computer worm (virus). He realized that it was possible for a computer program to move across a network, leaving a small trail (series of signs) wherever it went. He named the program Creeper, and designed it to travel between Tenex terminals on the early ARPANET, printing the message "I'M THE CREEPER: CATCH ME IF YOU CAN."
An American computer programmer named Ray Tomlinson, the inventor of email, was also working for BBN Technologies at the time. He saw this idea and liked it. He tinkered (an act of attempting to repair something) with the program and made it self-replicating "the first computer worm." He named the program Reaper, the first antivirus software which would found copies of The Creeper and delete it
Nowadays, viruses were deadlier, more invasive, and harder to control. We have already experienced cyber incidents on a massive scale, and 2018 isn't close to over. The above is to name a few, but these attacks are enough to prove that cybersecurity is a necessity for corporations and small businesses alike
Cyber Security Goals
The objective of
Cybersecurity is to protect information from being stolen, compromised or
attacked. Cybersecurity can be measured by at least one of three goals-
1.
Protect the confidentiality of data.
2.
Preserve the integrity of data.
3.
Promote the availability of data for authorized users.
These goals form the
confidentiality, integrity, availability (CIA) triad, the basis of all security
programs. The CIA triad is a security model that is designed to guide policies
for information security within the premises of an organization or company.
This model is also referred to as the AIC
(Availability, Integrity, and Confidentiality) triad
to avoid the confusion with the Central Intelligence Agency. The elements of
the triad are considered the three most crucial components of security.
The CIA criteria are one
that most of the organizations and companies use when they have installed a new
application, creates a database or when guaranteeing access to some data. For
data to be completely secure, all of these security goals must come into
effect. These are security policies that all work together, and therefore it
can be wrong to overlook one policy.
The CIA triad are-
1. Confidentiality
Confidentiality is roughly
equivalent to privacy and avoids the unauthorized disclosure of information. It
involves the protection of data, providing access for those who are allowed to
see it while disallowing others from learning anything about its content. It
prevents essential information from reaching the wrong people while making sure
that the right people can get it. Data encryption is a good example to ensure
confidentiality.
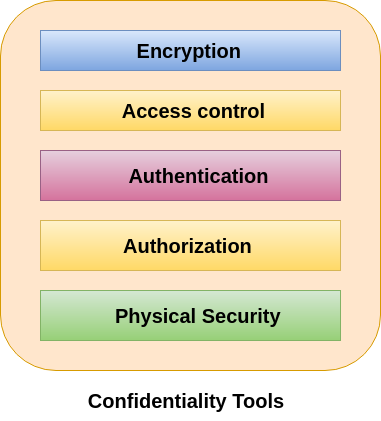
Tools for Confidentiality
Encryption
Encryption is a method of
transforming information to make it unreadable for unauthorized users by using
an algorithm. The transformation of data uses a secret key (an encryption key)
so that the transformed data can only be read by using another secret key
(decryption key). It protects sensitive data such as credit card numbers by
encoding and transforming data into unreadable cipher text. This encrypted data
can only be read by decrypting it. Asymmetric-key and symmetric-key are the two
primary types of encryption.
Access control
Access control defines rules
and policies for limiting access to a system or to physical or virtual
resources. It is a process by which users are granted access and certain
privileges to systems, resources or information. In access control systems,
users need to present credentials before they can be granted access such as a
person's name or a computer's serial number. In physical systems, these
credentials may come in many forms, but credentials that can't be transferred
provide the most security.
Authentication
An authentication is a
process that ensures and confirms a user's identity or role that someone has.
It can be done in a number of different ways, but it is usually based on a
combination of-
- something the
person has (like a smart card or a radio key for storing secret keys),
- something the
person knows (like a password),
- something the
person is (like a human with a fingerprint).
Authentication is the
necessity of every organizations because it enables organizations to keep their
networks secure by permitting only authenticated users to access its protected
resources. These resources may include computer systems, networks, databases,
websites and other network-based applications or services.
Authorization
Authorization is a security
mechanism which gives permission to do or have something. It is used to
determine a person or system is allowed access to resources, based on an access
control policy, including computer programs, files, services, data and
application features. It is normally preceded by authentication for user
identity verification. System administrators are typically assigned permission
levels covering all system and user resources. During authorization, a system
verifies an authenticated user's access rules and either grants or refuses
resource access.
Physical Security
Physical security describes
measures designed to deny the unauthorized access of IT assets like facilities,
equipment, personnel, resources and other properties from damage. It protects
these assets from physical threats including theft, vandalism, fire and natural
disasters.
2. Integrity
Integrity refers to the
methods for ensuring that data is real, accurate and safeguarded from
unauthorized user modification. It is the property that information has not be
altered in an unauthorized way, and that source of the information is genuine.
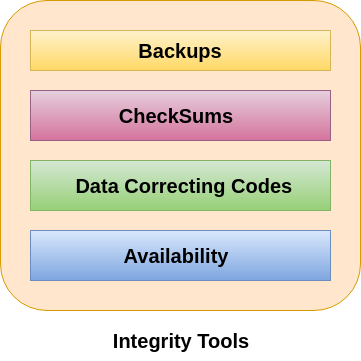
Tools for Integrity
Backups
Backup is the periodic
archiving of data. It is a process of making copies of data or data files to
use in the event when the original data or data files are lost or destroyed. It
is also used to make copies for historical purposes, such as for longitudinal
studies, statistics or for historical records or to meet the requirements of a
data retention policy. Many applications especially in a Windows environment,
produce backup files using the .BAK file extension.
Checksums
A checksum is a numerical
value used to verify the integrity of a file or a data transfer. In other
words, it is the computation of a function that maps the contents of a file to
a numerical value. They are typically used to compare two sets of data to make
sure that they are the same. A checksum function depends on the entire contents
of a file. It is designed in a way that even a small change to the input file
(such as flipping a single bit) likely to results in different output value.
Data Correcting Codes
It is a method for storing
data in such a way that small changes can be easily detected and automatically
corrected.
3. Availability
Availability is the property
in which information is accessible and modifiable in a timely fashion by those
authorized to do so. It is the guarantee of reliable and constant access to our
sensitive data by authorized people.
Tools for Availability
- Physical
Protections
- Computational
Redundancies
Physical Protections
Physical safeguard means to
keep information available even in the event of physical challenges. It ensure
sensitive information and critical information technology are housed in secure
areas.
Computational redundancies
It is applied as fault
tolerant against accidental faults. It protects computers and storage devices
that serve as fallbacks in the case of failures.
0 comments:
Post a Comment